Blog posts about WordPress on the bava in conversation with the great D’Arcy Norman? Party like it’s 2008!
@jimgroom I’d love to see how you fixed the xmlrpc thing. blog post on htaccess etc…?
— D’Arcy Norman (@dlnorman) July 30, 2015
Reclaim Hosting‘s Ramones server was experiencing some extremely high loads this afternoon, and D’Arcy gave Tim and I a heads-up on Twitter to let us know as much. The A-Team was on the job, and more than up to the task!  The first thing we check when we’re getting unusually high loads is the Apache Status in WHM (the GUI interface for managing a CPanel server). We look to see if there is one particular site getting hammered with requests—which is often, though not always, the case with random load spikes.
The first thing we check when we’re getting unusually high loads is the Apache Status in WHM (the GUI interface for managing a CPanel server). We look to see if there is one particular site getting hammered with requests—which is often, though not always, the case with random load spikes. 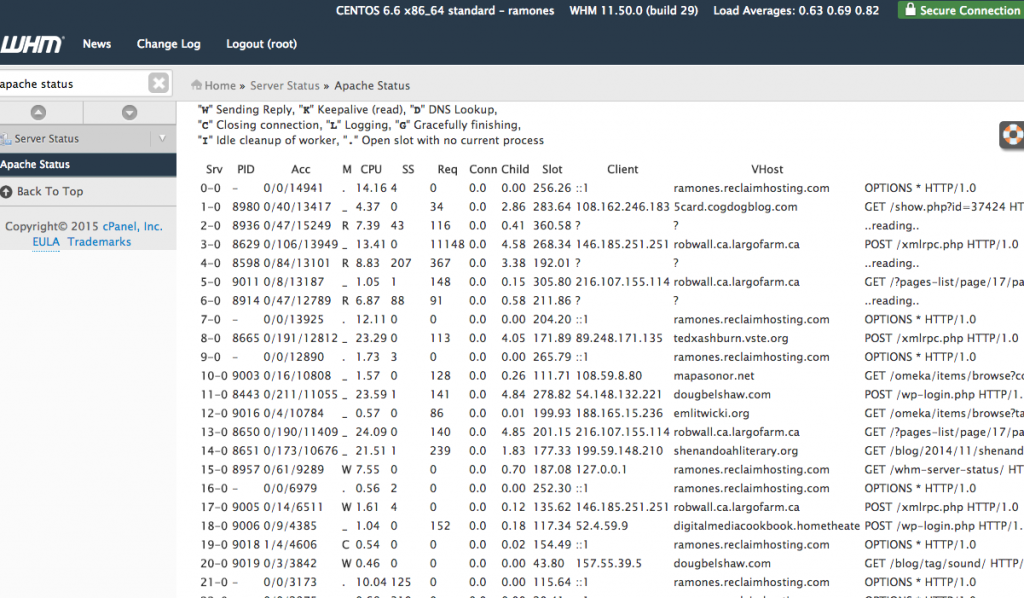 In the instance earlier today, one WordPress blog was getting hit very hard with login attempts, often referred to as brute force login attempts. But rathe than the wp-login.php file, it was the xmlrpc.php file which has been a vulnerability for years because it provides, in the words of my server sensei Tim Owens, “a huge target for brute force login attempts because it bypasses the traditional wp-login.php and goes right for logging in via API.” This was precisely the case with the intense load on Ramones this afternoon.
In the instance earlier today, one WordPress blog was getting hit very hard with login attempts, often referred to as brute force login attempts. But rathe than the wp-login.php file, it was the xmlrpc.php file which has been a vulnerability for years because it provides, in the words of my server sensei Tim Owens, “a huge target for brute force login attempts because it bypasses the traditional wp-login.php and goes right for logging in via API.” This was precisely the case with the intense load on Ramones this afternoon.
Tim has started collecting snippets of code in our internal documentation, like the one below, that we can just add to the .htaccess file in the affected WordPress install to block all calls to xmlrpc.php. Below is the code snippet we copied into .htaccess this afternoon that brought the load back down almost immediately. Hope you find it helpful.
<IfModule mod_setenvif.c>
<Files xmlrpc.php>
BrowserMatch "Poster" allowed
BrowserMatch "WordPress" allowed
BrowserMatch "Windows Live Writer" allowed
BrowserMatch "wp-iphone" allowed
BrowserMatch "wp-android" allowed
BrowserMatch "wp-windowsphone" allowed
Order Deny,Allow
Deny from All
Allow from env=allowed
</Files>
</IfModule>
ErrorDocument 403 "Access Denied"


I love it when a plan comes together.
AH PIDDY DA FOO DAT TRIES TO BRUTE-FORCE A RECLAIM SERVER!